For some reason, our web site has been copied.
Make sure to always visit https://www.rorohiko.com (secure) instead of http://www.rorohiko.com, so there is at least some checking.
I have no clear idea yet how it all fits together, but it looks like someone is trying something nasty, so I thought it better to document it.
It became apparent when our web site crashed two days in a row. After some post-mortem analysis, it looks like it ran out of memory after being tackled by what might be an overly greedy robot, or possibly (probably) someone with nefarious purposes.
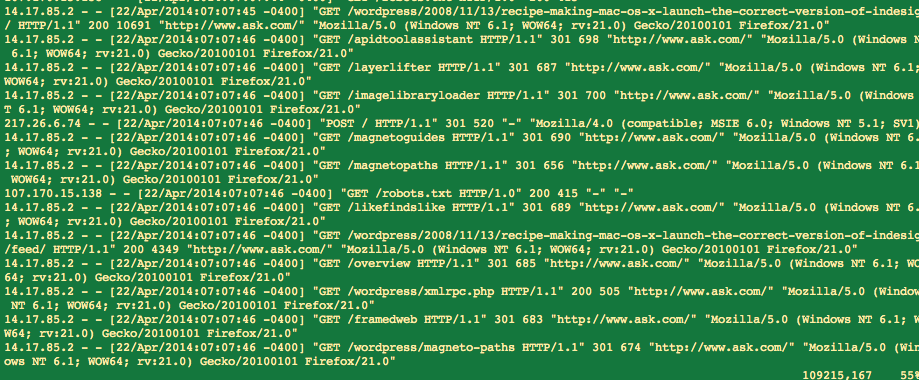
First of all, our web site got flooded by requests two days in a row, both days around the same time. The IP addresses where the requests are coming from are located in China. By the looks of it, it is a very aggressive scraper which tries to capture all our content.
That causes our server to crash: too many apache instances get launched, each connecting to our WordPress/MySQL database, and eventually there is not enough memory for our wee server, and something dies – most often the MySQL server.
At first, I thought I’d be fine by simply blocking those IP addresses.
Here’s a sample: the address 14.17.85.2 starts going through our pages. It continues like that for about 10 minutes, after which our server crashes. The same happened the next day, this time from two IP addresses at the same time, 183.61.189.130 and 183.61.189.139. In both cases the requests pretend to come from http://www.ask.com, but the IP addresses are physically located in China.
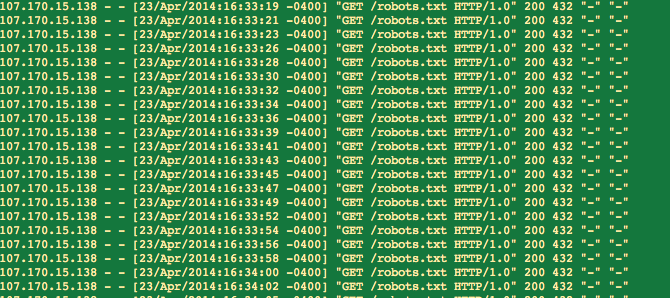
In our logs, I also found an extremely frequent visit of robots.txt from another IP address: it fetches our robots.txt file every few seconds.
On a whim, I visited that address in my browser.
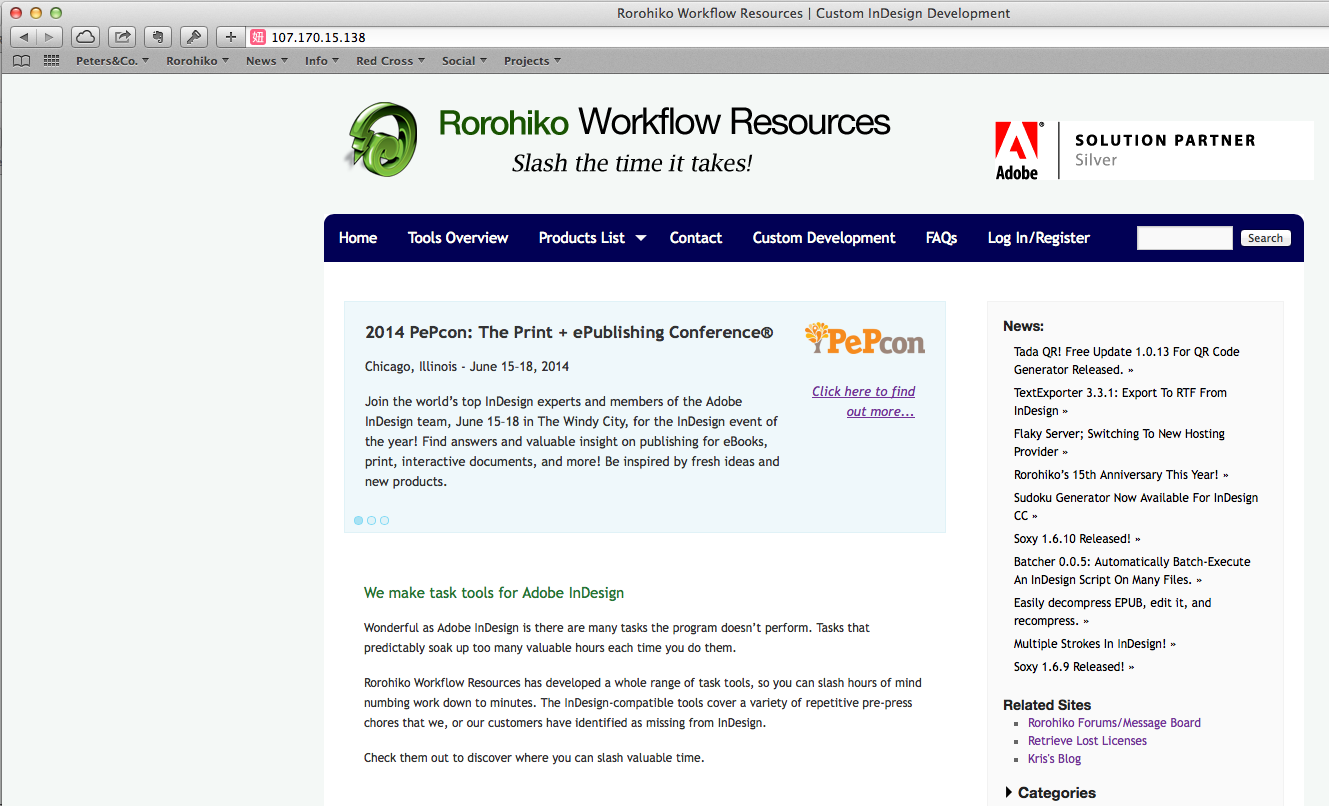
Surprise: I stumble upon a look-alike of our own web site. The only give-away is the icon in the address bar: it’s some Chinese character.
So, I blocked the IP address 107.170.15.138 from visiting our server via the firewall. That put a stop to the relentless fetching of robots.txt.
Strangely enough, when I re-visited the exact same IP address a little while later it now showed a totally different look:
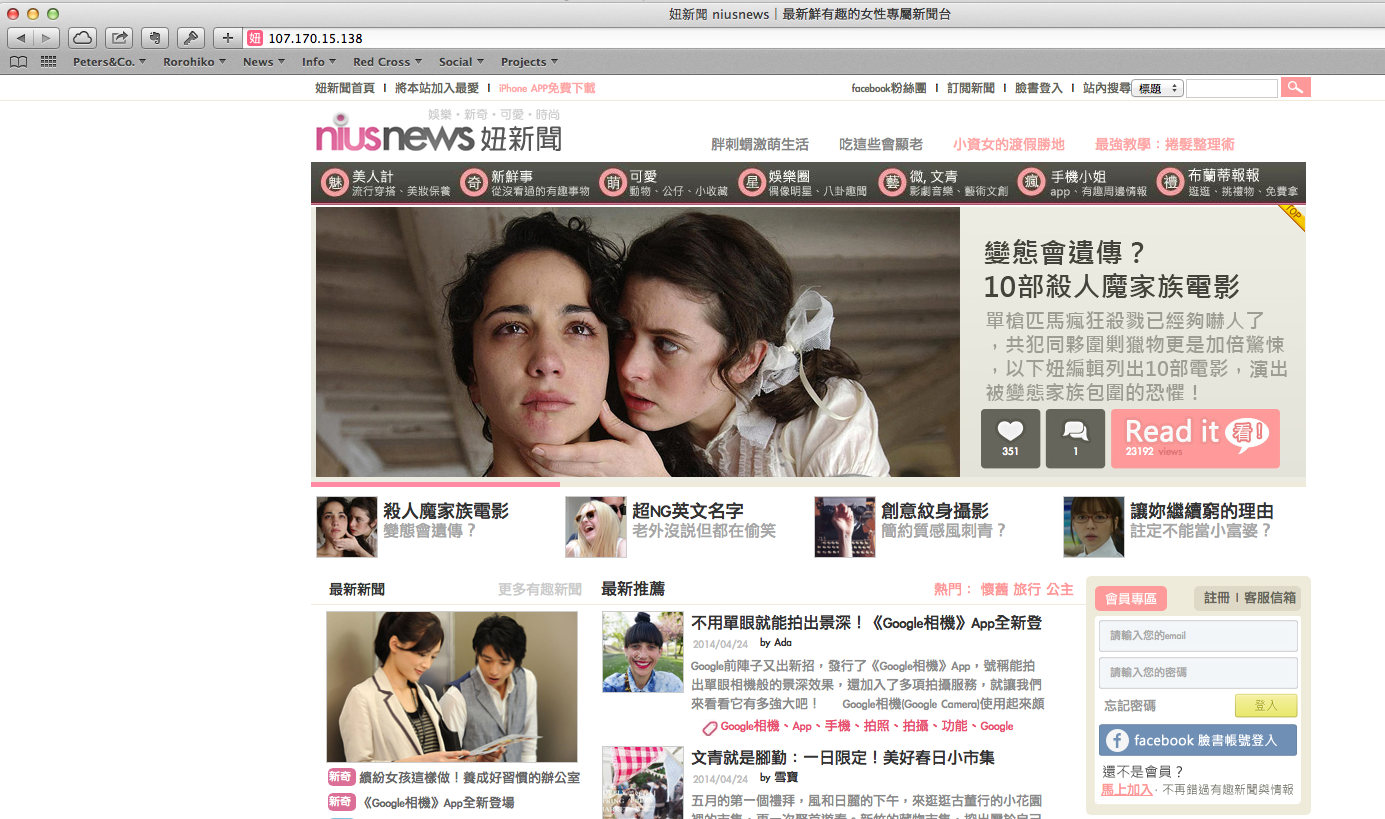
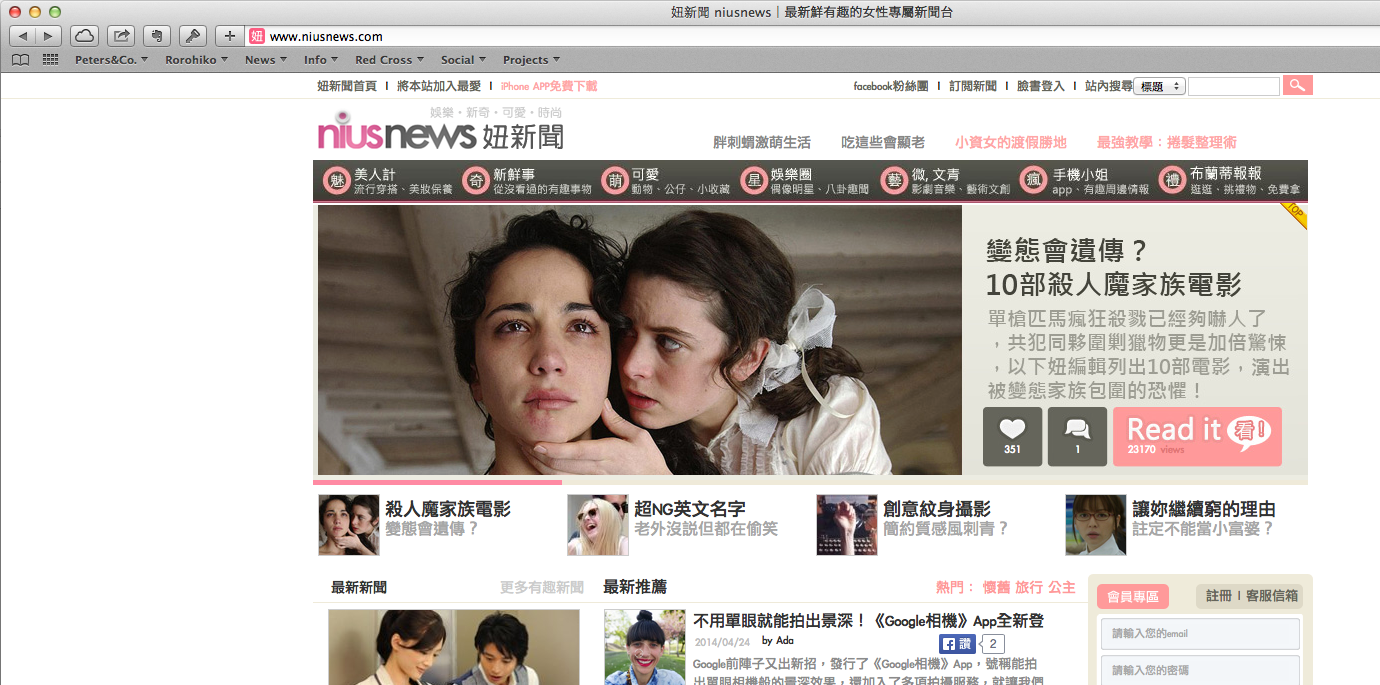
This looked like a ‘real’ web site. But it is not – I did a bit more digging, and the ‘real’ web site is called www.niusnews.com.
So, the same IP address that ‘faked’ www.rorohiko.com is now pretending to be www.niusnews.com.
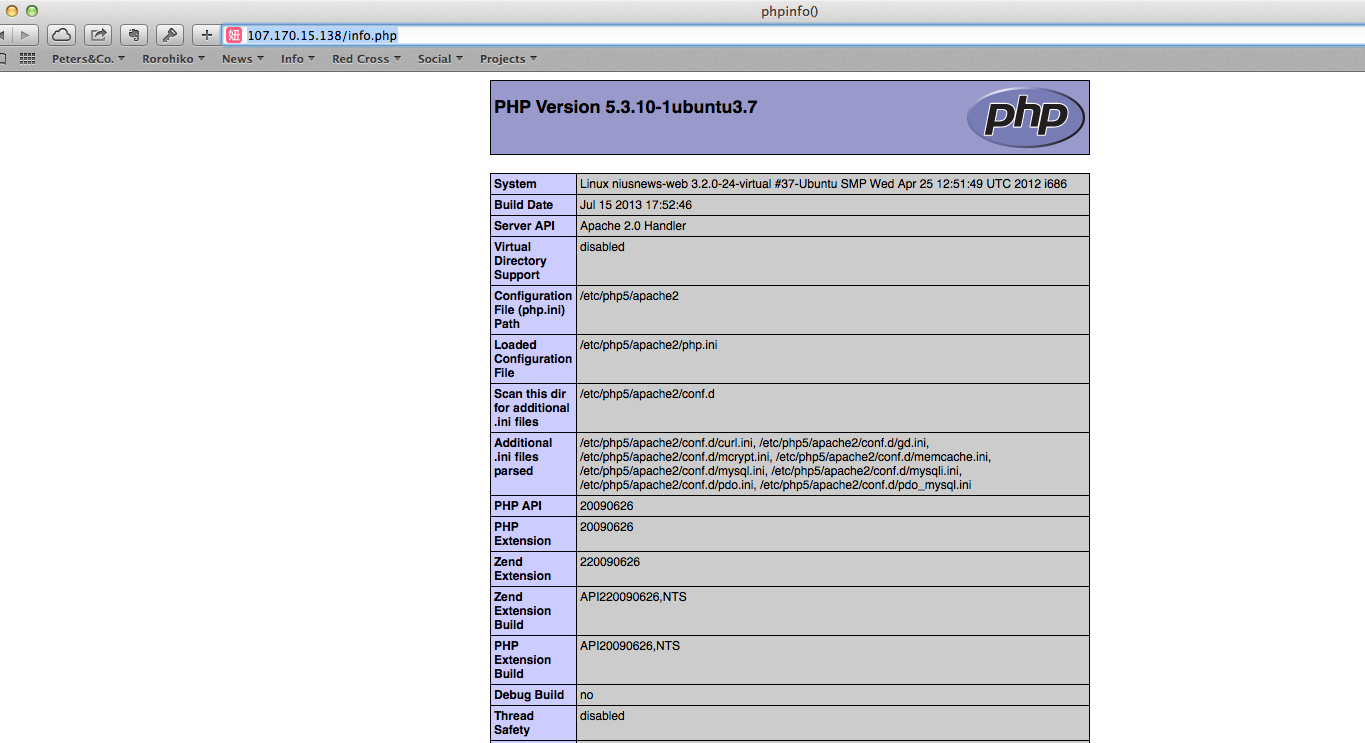
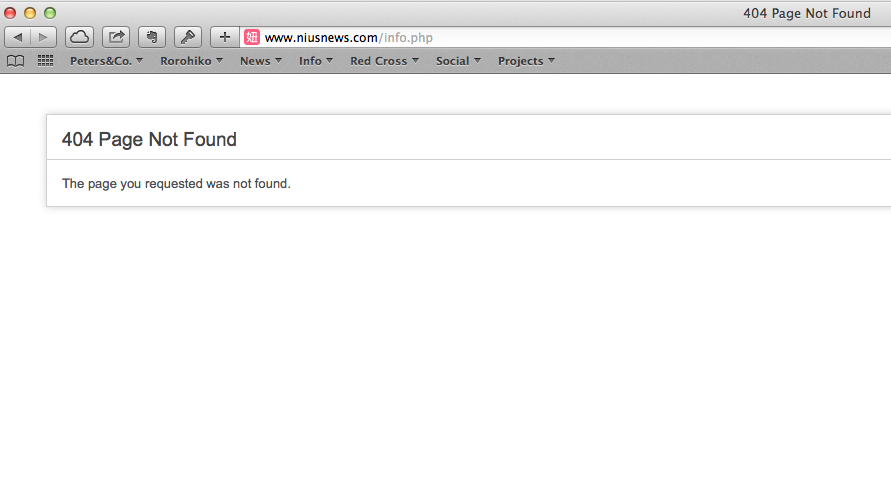
The 107.170.15.138 is running a Linux server, and there is an info.php. So, accessing http://107.170.15.138/info.php gives some insights, whereas on the ‘real’ http://www.niusnews.com/info.php does not exist.
What does this all mean? I don’t know, but by the looks of it, I’d say someone is trying to build ‘fake’ web sites that look like the originals. Probably the idea is to get unsuspecting people to visit the fakes and be hit by nasties.
So, all I can say: be very careful: there are fake web sites out there…